CryptoLocker Virus Holds Your Data Files for Ransom
CryptoLocker is a form of malicious malware known as cryptoviral extortion ransomware. This scheme encrypts key data files on a computer and all the network drives you have access to, making them inaccessible until you pay a ransom to obtain a decryption key. The virus does not reveal itself until after it has encrypted your data and your computer is on the internet so that the virus can identify your system to the encryption server run by the attackers.
Even up-to-date anti-virus applications do not defend against CryptoLocker. While you can remove the virus from your computer, there are no patches to undo the encryption damage.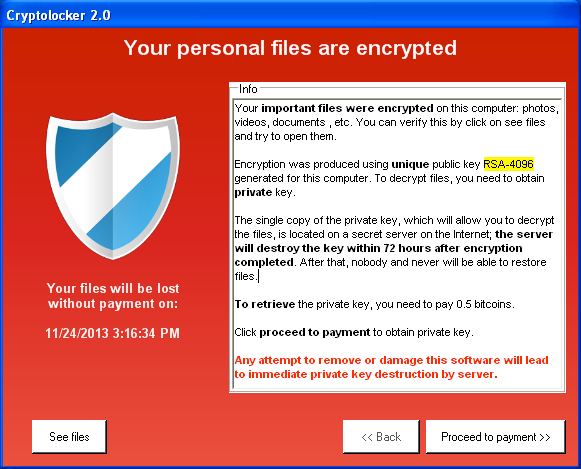
The only way to get your files back is to pay the ransom or restore the files from backup.
How do you get CryptoLocker?
There are three ways that you might get this virus.
Opening an email attachment with an infected file or downloading a malicious file from a website.
Browsing a malicious website that exploits vulnerabilities in an out-of-date version of Java.
Having malware already on your computer that the criminals use as a backdoor to copy CryptoLocker onto your computer.
How will you know you have CryptoLocker?
If your computer is infected with this malware, you’ll notice two things.
A red banner will show up on your computer monitor warning you that your files are encrypted – but if you send money (usually $300) to a given email address within a specified time period, you will be given the decryption key to restore your files.
You won’t be able to open Microsoft Office files, database files, images and other common documents. Instead, you’ll get a warning such as “Excel cannot open the file [filename] because the file format or file extension is not valid.”
How can you get your data back?
There are only two ways to restore access to your data.
You can pay the criminals but be aware that you may not get your data back. Generally, the attackers require payment using some untraceable form such as bitcoins or prepaid debit card. What’s surprising is that, up to this point, the criminals have provided the decryption key.
The only other option is to restore your files from backup.
What can you do to prevent future virus infections?
If you use TronixSystem’s complete IT management services, you’ve already taken the first step. You already benefit from the following proactive services:
Security patching. Our automated systems and trained techs patch your operating systems and software to keep them up to date with the latest security and performance updates. And we do this during the overnight hours and on Sundays to minimize the disruption to your business.
Anti-virus Monitoring. Most people have some anti-virus program, but how do you know it’s effective? TronixSystem provides 24×7 monitoring to make sure your anti-virus is active and up to date, and resolves any uncovered issues.
Regular scanning for malware. Our automated systems work in the background to sniff out potential malware, security holes, and exposure to viruses.
Backup monitoring and testing. Of course you have backups! But are you monitoring, verifying, and testing them on a regular basis? TronixSystem monitors the status of all backups 24×7 and resolves issues as alerts are received. We also test restoring data from backups on a monthly basis.
 Spam filtering. Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails. Minimizing spam using an effective spam blocking system will reduce overall exposure to these malicious sources.
Spam filtering. Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails. Minimizing spam using an effective spam blocking system will reduce overall exposure to these malicious sources.
Content filtering. Viruses can be downloaded by simply browsing malicious web sites or downloading and opening files from these sites. Internet content filters can be implemented to block access to these sites on a selective or company-wide basis.
Manage user access privileges. Viruses get installed and spread by exploiting the high level of access control assigned to most users. Allowing users to have full administrator privileges gives a virus full rights to install itself and infect a users’ computer, along with all systems and files to which that user has access and rights. Implementing the best practice of “least access right” required to use a company’s key business applications will minimize this security exposure and the risk of viruses.
Feel free to call us to discuss any of these protective and preventive services. We will be happy to consult with you on a complimentary basis.