Your Key to Secure Data
In last week’s blog post, we described the government regulations to protect sensitive data and the penalties imposed for a data breach. Keeping data secure is important not just to the individuals affected, but also to the success of your business. What can you do to protect your clients’/patients’/HR information and follow best practices? The most powerful tool you can use, to protect electronic credit card information, ePHI, personnel records and other electronic sensitive data, is encryption.
Encryption to Protect Data
Lost or stolen portable devices is one of the primary causes of data breaches. However, if the data on the lost device is encrypted, the loss is not considered to be a data breach. Therefore, the most effective solution to protect data and avoid a security breach is to encrypt data stored on these devices.
 To protect private information used in any business, the use of encryption is required on the computers and devices being used (including back-up devices), as well as for cloud applications. It is also required on websites which collect personal information, such as those used when individuals make credit card purchases on the web, do online banking, or access a patient portal.
To protect private information used in any business, the use of encryption is required on the computers and devices being used (including back-up devices), as well as for cloud applications. It is also required on websites which collect personal information, such as those used when individuals make credit card purchases on the web, do online banking, or access a patient portal.
How Encryption Works
Encryption uses a mathematical algorithm to scramble the text so that it cannot be read. This prevents the sensitive data from being accessed without providing the key to convert the information back to its readable form. The key could be a secure password or it could require a secure methodology called two-factor authentication.
Single-factor authentication requires only your username and one password. Two-factor authorization (2FA) adds a second level of authentication, requiring the user to have two out of three types of credentials before being able to read the encrypted data. The three possible types of credentials are a PIN number, a fob, and a biometric match.
In a secure system, access attempts are locked out after a specified threshold is reached to prevent unauthorized access. In addition, lockout events are logged for auditing purposes.
There are two types of data to encrypt, data at rest and data in motion (also called data in transit). Data at rest is data that is stored in digital form, such as databases, spreadsheets, backups and archives. Data in motion is information that is moving through a network, such as data being backed up from a laptop to a central server. An email is also classified as data in motion between the time that it is sent until the time that it reaches the recipient’s email host.
The encryption software to use depends on the type of data and what needs to be encrypted. There are several data encryption tools available within the operating systems and from third party vendors for use on a desktops, laptops, and removable storage devices. Encryption software can encrypt the entire hard disk, or specific files or folders. Microsoft includes a program called BitLocker on the higher end, professional versions of Windows 7 and Windows 8 which can be configured to encrypt an entire volume of data on a hard disk or removable drive.
For organizations, there are central management tools to lock and unlock several drives remotely, and to wipe a drive clean if it is stolen. Encryption software is also available for sending sensitive information via email.
Secure Websites and Email
secure email - TronixSystem WisdomCloudWhen private information is entered on the web, the URL of the website requesting the information should begin with “https” instead of “http”. Hypertext Transfer Protocol Secure (HTTPS) provides bi-directional encryption of communications between a client and server. The “s” means that the site is secure.
When sending an encrypted email, the sent email is intercepted by an encryption system which holds the email in an encrypted state. The system then sends an unencrypted notification to the email recipient notifying the recipient that an email is waiting. The recipient clicks on the link and then has to securely log in to download the email. The URL for the login screen begins with https indicating that the login is secure. secure email login - TronixSystem Wisdom Cloud
TronixSystem provides encrypted email services to our clients through our WisdomCloud. Call us to discuss how we can add optional encryption to your email communications flow.
Encrypted Backups
Backup devices also need to be encrypted. TronixSystem’s TSP backup appliance uses advanced encryption technology which ensures that data cannot be accessed while stored on the appliance, while being transmitted to an offsite data center and while stored at the data center. If a TSP backup appliance is stolen, TronixSystem has the ability to remotely wipe all data stored on the device.
Protecting a Stolen Smartphone
If you use a smartphone for business, your phone may contain personally identifiable private data related to your clients, patients or staff. Thus, you may need to encrypt the data stored on your device. It is also important to set up a password to lock your device. If you send emails containing patient or financial information, you will need to send encrypted emails to comply with government regulations. If your smartphone is lost or stolen, you can protect data by wiping it remotely. Remote wipe sets the phone back to its factory settings, thus clearing any data on the device. (Note: Depending on the device, if a device is wiped, personal data and photos will also be removed, in addition to the company information).
TronixSystem offers mobile device management (MDM) services to manage the security of smartphones, iPads and other portable devices and provides remote wipe services to our clients for their corporate devices.
The Key
Encryption is the key to secure data on websites, in email, on laptops, on backup devices, on smartphones, and on other devices. Encryption keeps personal information secure because encrypted data cannot be accessed without the encryption key required to make the data readable. As we noted in our blog post about HIPAA Breaches, Business Associates, and Encryption, the only exception to the HIPAA breach notification requirement is if the PHI disclosed was secured with encryption technology.
Does your company use encryption to protect the data stored and transmitted on your systems? TronixSystem can help you design a solution to secure your data, regardless of where that data may be. Call us to get started with this critical security requirement.


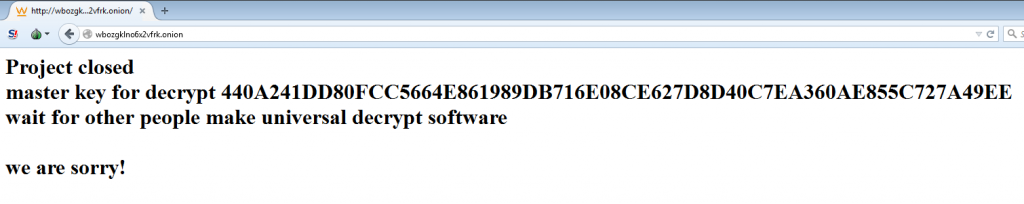
 To protect private information used in any business, the use of encryption is required on the computers and devices being used (including back-up devices), as well as for cloud applications. It is also required on websites which collect personal information, such as those used when individuals make credit card purchases on the web, do online banking, or access a patient portal.
To protect private information used in any business, the use of encryption is required on the computers and devices being used (including back-up devices), as well as for cloud applications. It is also required on websites which collect personal information, such as those used when individuals make credit card purchases on the web, do online banking, or access a patient portal.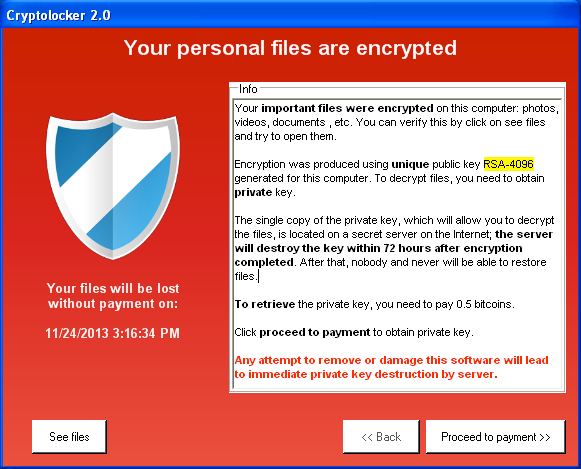
 Spam filtering. Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails. Minimizing spam using an effective spam blocking system will reduce overall exposure to these malicious sources.
Spam filtering. Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails. Minimizing spam using an effective spam blocking system will reduce overall exposure to these malicious sources.